The Iran Project
: It's been a long time since we all came to know that cyber pollution in Iran is so high that in some cases, it has gained the first place in the world [1]. Here we are going to concisely examine the issue.
Thursday 7 March 2024 - 15:09
Story Code : 416933
Source : Virgool
A glance at cyber attacks and contamination in Iran
Mohsen Tahmasebi
Reports of cyber attacks and contamination in Iran
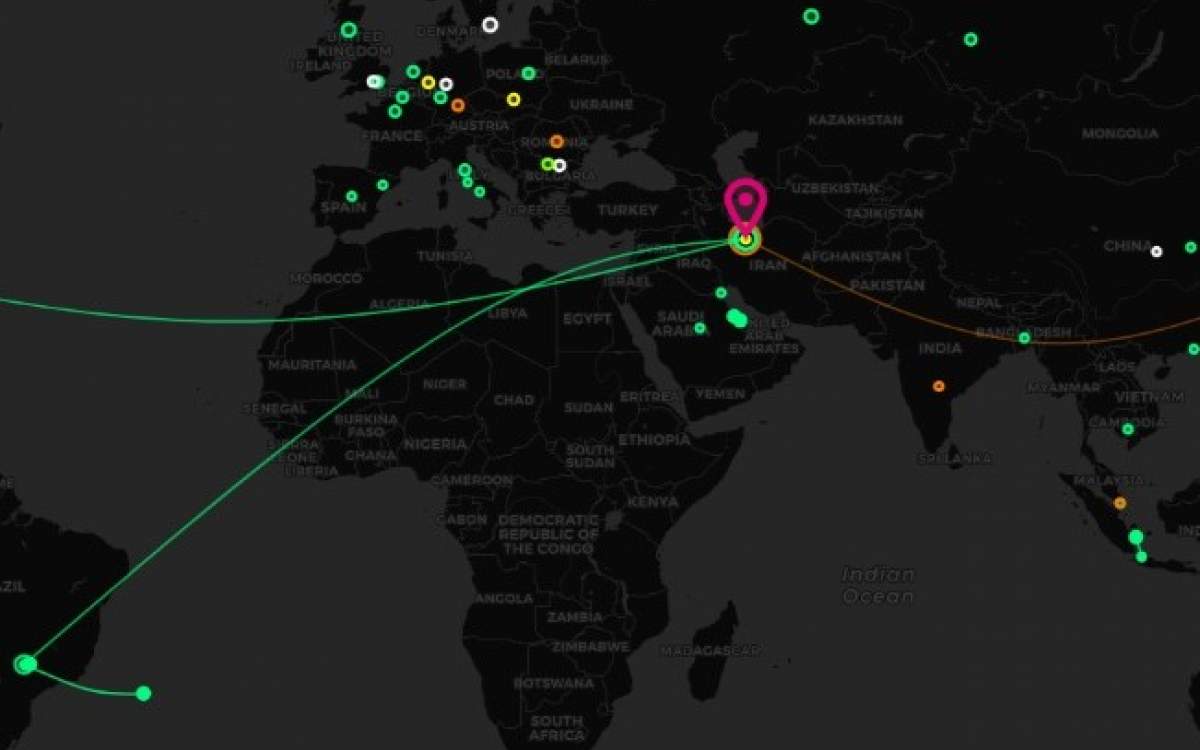
Over the past years, I conducted some research mainly on Android malware [2][3][4], which shows the situation in Iran. But the extent of pollution in Iran is also seen in foreign reports; From Cloudflare's report on the type of traffic coming from Iran [5] (its reason is still unclear) to Iran's number one ranking in mobile malware contamination [1].
 Cloudflare radar report of traffic coming from Iran
Cloudflare radar report of traffic coming from IranThis contamination does not only affect the user, but it may cause attacks from the user's infected system, which wastes the volume of the Internet, puts pressure on the network, and causes pressure on the infrastructure of the attack destination. Or even, in some cases
Such infections cause sensitive information to be exposed and an organization to be hacked, for example, this is one of the possibilities regarding the method of hacking SnappFood [6].
 An image of information stolen from infected system of a SnappFood staff [6]
An image of information stolen from infected system of a SnappFood staff [6]But the thing that is less discussed in the news and public space is the hacking of devices other than phones, PCs and servers. More specifically, in recent years there have been many threats against Internet of Things (IoT) devices and things like online cameras and modems, because these devices are not necessarily designed to be safe, they are constantly connected to the Internet and are rarely updated. In the following, we will see that contrary to what many people think, these attacks and pollution are common in Iran.
Research method
In this research, we used different methods: two large honeypots [7] in two Iranian datacenters, a passive internet sensor on my home network, internet scanners and crawlers, and open threat intelligence sources.
The information obtained from these methods is collected and analyzed, and significant cases are mentioned in this post after further research.
It should be noted that this is a very small project with very little time, resources, and data, although interesting things have been found at this scale.
Contamination of swebites and attacks on users
uring this research, we came face many Iranian sites (especially WordPress sites) that were infected with PHP malware due to security weaknesses such as the use of vulnerable or cracked plugins. These malwares cannot be removed easily and by injecting themselves into different parts of the infected site, they prevent complete removal.
In a particular example, we found a malware [8] that had infected a famous Iranian site and tricked the visiting user into downloading a Windows malware with a fake browser update page. With further investigation, it was realized that this Windows malware is probably one of the RedLine Stealer Trojans [9].
The interesting thing about this malware is that it is Malware as a Service; This means that this Trojan is sold to hackers along with its necessary tools and infrastructure and hackers infect users with this trojan in different ways to steal users' information and carry out attacks through their system without the technical concerns of infrastructure management.

Malware communication graph
Massive banking malware campaigns
Recently, a report was published by Zimperium about banking malware in Iran [10] and it would be useful to address it here.Iranian banking malware has become much more advanced than a few years ago. These malwares, which generally install themselves as mobile banks or Android applications, empty the victim's bank account by listening to banking SMS or getting login information to the user's mobile bank. According to Zimperium's research, these hacker groups are becoming more advanced day and day.
 Based on my examinations a few years ago, most of these malwares are spread inside Telegram, and it is recommended not to install any Android apps from Telegram. Given the changes and progress of Iranian malware in recent years, investigating and hunting these threats can lead to interesting results.
Based on my examinations a few years ago, most of these malwares are spread inside Telegram, and it is recommended not to install any Android apps from Telegram. Given the changes and progress of Iranian malware in recent years, investigating and hunting these threats can lead to interesting results.Common SMS Bombing attacks in Iran
This attack is relatively common in Iran, and you or one of your friend may have been a victim of this attack. In this attack, the victim receives authentication and login SMS from many sites. Sometimes the number of these text messages reaches tens of SMS per minute, which causes fear in the victim. These types of attacks have no security risk for the user and are used only to scare the victim.
The important thing about these attacks in Iran is that they are offered as a service. This means that anyone can carry out this attack against a person by paying a fee to the hackers who do this. Apparently, the income of this work is so much that one or more Iranian groups are full-time reverse-engineering the SMS sending APIs of Iranian sites and services to use in these attacks. Due to the high volume of SMS sent, the sites and small services that are victims of these attacks suffer financial losses.
To deal with this attack, there is nothing the user can do, but sites and services should apply rate limit on the relevant APIs as much as possible to keep the level of damage low (of course, if they want, there are methods to reduce it to zero).It is worth mentioning that in two cases, I saw that the attacker's server is inside Iran, but the server providers are not interested in following up and preventing these attacks.
Secret of Internet scans coming from Iran: Wide contamination to Mirai family
From the first minutes of launching Honeypot, we noticed a lot of traffic from Iran. Further analysis showed that from the source of an Iranian ISP (AS50558) many scans are being done to SMB and TELNET ports. These scans are very common on the Internet, in fact, as soon as you connect to the Internet, requests from all over the world come to you. The purpose of some of these requests is to scan the entire Internet for research and security reasons, but most of the time, this is not the case. Most internet scans are done by hackers and infected systems, and their goal is to find vulnerable systems or systems with weak passwords. In fact, it is a race between hackers to find and infect vulnerable systems first.In this particular case, this ISP's remark made us suspicious of research and security scans:

The whois image of the ISP
But the volume of scans, scanned ports and executed commands suggested another scenario. In some cases, commands were executed to download and execute a file [11], which turned out to be Hajime malware [12]. This malware, which has similarities to the Mirai family [13], was activated amid the proliferation of the controversial Mirai malware around 2017 and began hacking vulnerable IoT devices on the Internet and of course, instead of exploiting it, it protected them against other similar attacks!This malware, which is still mysterious, infected about 300,000 devices in 2017, about 20% of which was in Iran [14]. Although Hajime somewhat secures the vulnerable device against similar attacks, it remains on the device and continues to infect other vulnerable devices. So far, Malicious operations of this malware have not been seen, but the active network and its complexity are still a threat (I recommend the study of this malware, especially its communication mechanism to those interested).
Despite seeing Hajime's signs of the attacks of this Iranian network, some cases, such as some specific scans, contradicted the behavior of this malware. This case was solved a few hours later, in the network where Hajime is so strongly present, probably Mirai and her friends are also there. A few hours later, we witness attempts to download and run Mirai and Bashlite malware from this network [15][16].
The extent of contamination in this network was very interesting for us, although a little later, very similar attacks were observed from other Iranian networks (with less intensity).
IoT malware infection in Iran: insecure modems and cameras
Seeing this level of IoT malware infection in Iran was not something we expected much. Attacks from telecommunication sources raised the possibility of contamination of modems and CCTV cameras. By examining one of the source IPs of these attacks, which was suspected of being infected with Mirai malware, we encountered a login page for a vulnerable online camera:

Information of one of the IPs of the origin of the attack
 Camera login page on the same IP Due to the small size of our infrastructure, the threat intelligence resource review revealed a better picture of the level of contamination:
Camera login page on the same IP Due to the small size of our infrastructure, the threat intelligence resource review revealed a better picture of the level of contamination:
Attacks from Iran on Internet network
Malware like the Mirai family by brute force devices with weak passwords and exploit vulnerable devices, turning them into bots to spread infection and DDoS attacks. One of the interesting points that was seen was relatively wide scans on port 7547 from the source of Iranian infections, which could be an attempt by the Mirai family of malware to exploit TR-069 on old modems [17].In addition to Iran, similar contaminations with significant extent were observed in other countries of the Middle East. Considering the small scale of our infrastructure, it was not possible to have a good estimate of the contamination level of such malware in Iran, but given the ratio of registered attacks to our scale, it can be said that the level of contamination is not low.
Brute force attacks on SSH and contamination of Iranian servers
A few examples of XorDDoS infection and SSH scanning were seen in Iran [18], which was not far from expected. The interesting case was the brute force attacks on SSH originating from America and several other countries (including Iran) with Iranian usernames and passwords such as Ali, Arman and Mohammad. Regarding the high ratio of these cases compared to the rest of users and passwords, it seems that in some cases hackers are using customized password lists for attack targets, which was an interesting point.
Hack miners and systems for mining
This was a very well-known case that was almost never seen in Iran. In many cases, hackers try to install miners by attacking SSH, TELNET, and ADB. In some cases, they check whether the hacked device is a miner or not. The case of ADB was interesting because the number of attacks was higher than expected. In this attack, the hacker was looking for Android devices that have ADB over Network enabled and exposed, and after collecting some information, he installed and ran a miner program on the hacked device [19].
WannaCry
One of the honeypots we used simulated a system with an open and vulnerable SMB. To our surprise, the famous WannaCry ransomware was seen many times [20] and it was interesting to us that this virus is still alive.
Reaction of of Iran's cyber security institutions to cyber pollution
After seeing the amount of contamination to the Mirai family and similar examples, I was interested to know the reaction of Iran's cyber security institutions. I searched the names of these malwares on the Maher Center website and a few other websites and found nothing except a few translated news (related to the peak of contamination in 2017). Not only now, but also there are no reports of these contaminations in Iran when 20% of Hajime's contamination was in Iran.
This also applies to the mentioned extensive banking malware campaign, it is interesting that an American company finds and documents such a campaign (which is specific to Iran) while there is no internal report about it before that.
Advice for users
You may ask, aside from all this, what can I do as a normal user to maintain my cyber security?
- The short answer to this question is that in the world of cyber security, your enemy as a normal user is three things:
1. Old and unupdated software and hardware
2. Weak passwords
3. Incaution in using the Internet (installing software from unknown sources, clicking on unknown links, logging in to any site, etc.)
Observaning these things will not eliminate all risks, but it may eliminate more than 90% of the risks faced by a normal user on the Internet
Final Word
This small project was very enjoyable for us. Of course, these are not all the current threats in Iran (in fact, they are not all the ones we found, more than eighty gigabytes of raw data were recorded and analyzed, and only the interesting points that drew our attention were mentioned in this article), they are not even among the most important. But for me personally, as a weekend project, it was very informative and interesting, for example, I learned that changing and distorting the fingerprint of a honeypot can significantly improve the results. I hope you enjoyed reading this post!
[1] https://www.statista.com/statistics/325201/countries-share-of-malicious-attacks/
[2] https://vrgl.ir/r1lgK
[3] https://vrgl.ir/MrAQ0
[4] https://vrgl.ir/AmA4u
[5] https://radar.cloudflare.com/ir
[6] https://www.infostealers.com/article/mysterious-hacker-strikes-iran-with-major-cyberattacks-against-industry-leading-companies/
[7] https://fa.wikipedia.org/wiki/%D9%87%D8%A7%D9%86%DB%8C%E2%80%8C%D9%BE%D8%A7%D8%AA
[8] 7c14b7f423e9554f9157d1abb6a62708b6f9b99fa0ad657bd69816a6bf4732cd
[9] https://malpedia.caad.fkie.fraunhofer.de/details/win.redline_stealer
[10] https://www.zimperium.com/blog/unveiling-the-persisting-threat-iranian-mobile-banking-malware-campaign-extends-its-reach/
[11] a04ac6d98ad989312783d4fe3456c53730b212c79a426fb215708b6c6daa3de3
[12] https://en.wikipedia.org/wiki/Hajime_(malware)
[13] https://en.wikipedia.org/wiki/Mirai_(malware)
[14] https://www.kaspersky.com/about/press-releases/2017_300000-obeying-devices-hajime-is-conquering-the-internet-of-things-world
[15] 7e8e33efdc8bab0d130eaf05b6dd7330c795cdaae468c11d8da807cd37a5a828
[16] a108ff340f5256cc17c1e8345aacc3cf6c91987a1884957ea75df6d23281480b
[17] https://www.qacafe.com/resources/home-router-attack-tr-069-vulnerability/
[18] ea40ecec0b30982fbb1662e67f97f0e9d6f43d2d587f2f588525fae683abea73
[19] 76ae6d577ba96b1c3a1de8b21c32a9faf6040f7e78d98269e0469d896c29dc64
[20] 64bb708b31b4b043018457c1098465ea83da7d6408c7029b2f68c333fc25891c
Reporter : Editorial of The Iran Project
# Tags